So you’re surfing the internet, minding your own business, and suddenly a message pops up that warns “you’re infected”. It is true? Sometimes. Unfortunately, these days the fake AV software looks more real than ever.
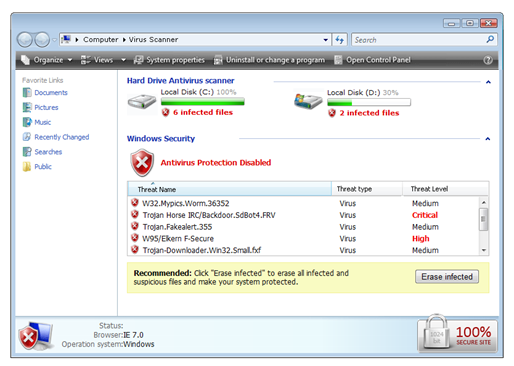
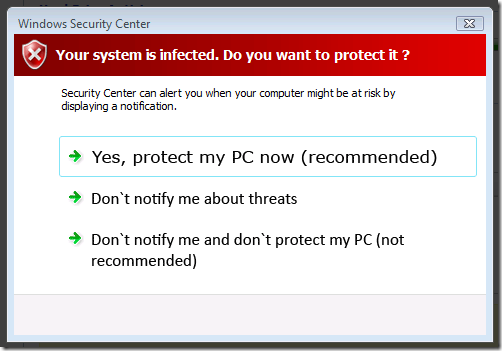
Here’s a good example of some fake AV that looks fairly convincing:
At first glance, a lot of people see this and believe they’re actually infected.
To make matters worse, even if you don’t click on the “Erase infected” button, after a few moments another window pops up:
Sadly, many users click “Yes, protect my PC now” and then it’s too late.
How Can You Tell It’s Fake?
Other than the obvious (knowing the name of the REAL antivirus software you have installed and knowing what it looks like), there are numerous ways to spot the fake AV. Get a well known antivirus such as Zonealarm mobile Security.
Browser version:
(This machine has IE8, Fake AV says IE7) 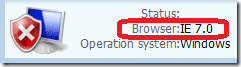
Number of drives / letters:
(This machine doesn’t have a D: drive) 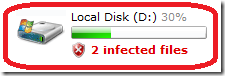
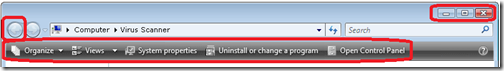
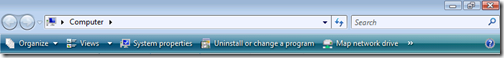
Incorrect navigation bars:
(Fake AV displays a modified Vista navigation bar on Windows 7 machine)
|
Fake AV |
 |
|
|
 |
|
|
 |
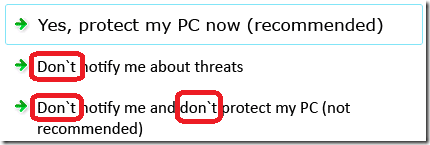
Typos or incorrect punctuation:
(Apostrophes pointed the wrong way)
Virus warnings that are displayed in a web page:
Solution:
Train your users by showing them what the REAL AV software looks like, and show examples what the fake software looks like.
The best way to show the real software in action is to trigger an actual virus alert. Then you can screenshot your current AV software. But instead of using a real virus to trip the alert, you can use the EICAR test file.
The EICAR is a harmless file that is available in several different file formats: 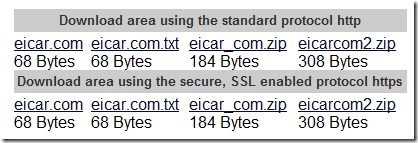
Here’s what it looks like inside the eicar.com.txt file: 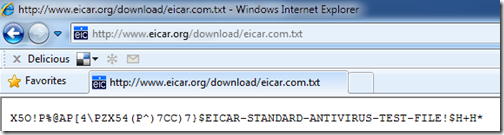
You can use the EICAR file to generate end-user documentation on what your real AV software screens look like.
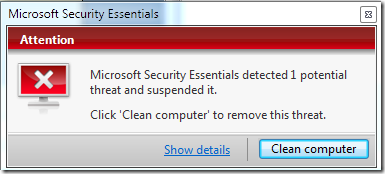
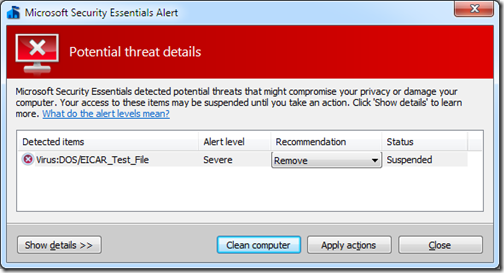
Example: Microsoft Security Essentials
1) Initial “infection” (triggered by clicking on the eicar.com.txt file)
2) After clicking Show details
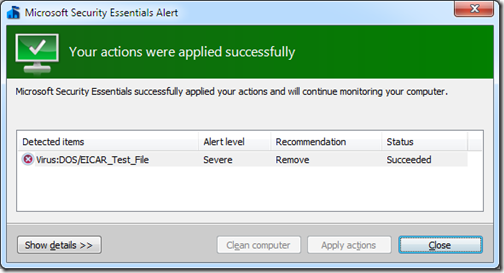
3) After clicking Clean computer
You can create a one-sheet “Virus Response Document” to print out and give to your users and include your phone number on the bottom. A little education up front can save lots of lost time and expense cleaning up after an infection or fake AV software removal battle.

He didn’t know that the FBI put out a warning this month about the threat of pop up security warnings. … The FBI states that those pop up messages contain "scareware", fake or rogue anti-virus software that looks authentic, but they are not. … The term scareware describes software