This little gem came in via email today. This is the kind of stuff that trips up users all of the time.
Note: Just because an email looks like Plain Text doesn’t mean that it is.

"Building Better Geeks Since 2004"
So you’re surfing the internet, minding your own business, and suddenly a message pops up that warns “you’re infected”. It is true? Sometimes. Unfortunately, these days the fake AV software looks more real than ever.
Here’s a good example of some fake AV that looks fairly convincing:
At first glance, a lot of people see this and believe they’re actually infected.
To make matters worse, even if you don’t click on the “Erase infected” button, after a few moments another window pops up:
Sadly, many users click “Yes, protect my PC now” and then it’s too late.
How Can You Tell It’s Fake?
Other than the obvious (knowing the name of the REAL antivirus software you have installed and knowing what it looks like), there are numerous ways to spot the fake AV. Get a well known antivirus such as Zonealarm mobile Security.
Browser version:
(This machine has IE8, Fake AV says IE7) 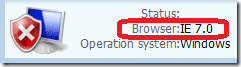
Number of drives / letters:
(This machine doesn’t have a D: drive) 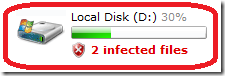
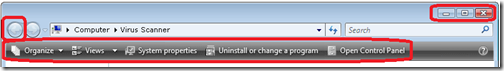
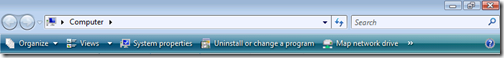
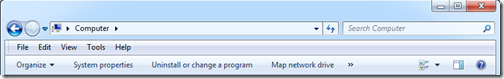
Incorrect navigation bars:
(Fake AV displays a modified Vista navigation bar on Windows 7 machine)
|
Fake AV |
 |
|
|
 |
|
|
 |
Typos or incorrect punctuation:
(Apostrophes pointed the wrong way)
Virus warnings that are displayed in a web page:
Solution:
Train your users by showing them what the REAL AV software looks like, and show examples what the fake software looks like.
The best way to show the real software in action is to trigger an actual virus alert. Then you can screenshot your current AV software. But instead of using a real virus to trip the alert, you can use the EICAR test file.
The EICAR is a harmless file that is available in several different file formats: 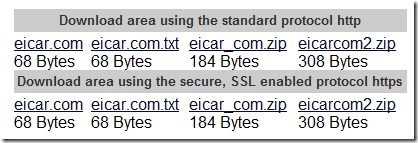
Here’s what it looks like inside the eicar.com.txt file: 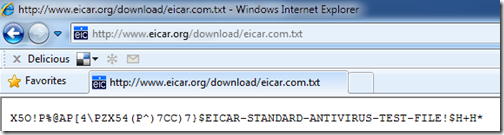
You can use the EICAR file to generate end-user documentation on what your real AV software screens look like.
Example: Microsoft Security Essentials
1) Initial “infection” (triggered by clicking on the eicar.com.txt file)
2) After clicking Show details
3) After clicking Clean computer
You can create a one-sheet “Virus Response Document” to print out and give to your users and include your phone number on the bottom. A little education up front can save lots of lost time and expense cleaning up after an infection or fake AV software removal battle.
 Bill Kam of Trend Micro is coming to Cincinnati to give a FREE live in-person training on Trend’s Worry Free products – best practices for install/configure and how to protect from things like “fakeav”, and new tools for the partner/IT Pro to use as well. He may cover some of the Worry Free 7 info shown recently in Taipei. There are some PPT’s comparing Trend with the competition on a level playing field showing memory and CPU utilization that he will go over. Bill will talk about all the features in Worry Free (some that many probably are not aware of).
Bill Kam of Trend Micro is coming to Cincinnati to give a FREE live in-person training on Trend’s Worry Free products – best practices for install/configure and how to protect from things like “fakeav”, and new tools for the partner/IT Pro to use as well. He may cover some of the Worry Free 7 info shown recently in Taipei. There are some PPT’s comparing Trend with the competition on a level playing field showing memory and CPU utilization that he will go over. Bill will talk about all the features in Worry Free (some that many probably are not aware of).
After the class, you can go online and take a “Certification” test (FREE) and with passing, you can get some benefits like showing up in a search on their site for a reseller in the area, website badges and marketing materials (think SBSC program). Good stuff!
Lunch is included for this event!
Event: Cincinnati SBS SIG – Trend Micro Live Training
Date: Saturday May 22, 2010
Time: 9:00 AM – 4:00 PM EDT
Venue: Max Technical Training
4900 Parkway Drive, #160
Mason, OH 45040
Registration URL: http://cinpa20100522.eventbrite.com/
 The news rags are online pointing fingers about who is to blame for the latest Windows issue nicknamed the blacK Screen Of Death (KSOD). Microsoft says it’s not a patch issue, Prevx apologized for initially blaming a patch. All I know for sure is that people want it fixed.
The news rags are online pointing fingers about who is to blame for the latest Windows issue nicknamed the blacK Screen Of Death (KSOD). Microsoft says it’s not a patch issue, Prevx apologized for initially blaming a patch. All I know for sure is that people want it fixed.
Oddly enough, about 10 minutes after reading the news I got a call from a client about a workstation exhibiting similar problems:
I’m not 100% certain that this is the same issue in the KSOD reports in the news, but it sounds similar.
WHAT DIDN’T WORK FOR ME
WHAT DID WORK FOR ME
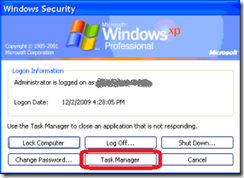
Here is the item that SuperAntiSpyware quarantined:
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\explorer.exe (Debugger – C:\Program Files\Microsoft Common\svchost.exe)
Again, I’m not saying for certain that this is the same issue others are reporting, but I wanted to pass along what I found in case others see similar issues. This is what worked for me – your mileage may vary.
UPDATE 12/2/2009:
Here is the link to the Prevx KSOD cleanup tool (I haven’t tried it though):
http://www.prevx.com/blog/140/Black-Screen-woes-could-affect-millions-on-Windows–Vista-and-XP.html
I saw this IM virus for the first time today:
WARNING – Don’t go to the URLs listed in this post, due to possible malware and NSFW content.
Followed a few minutes later by: 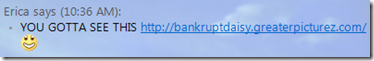
That’s from one of my sisters (so I see some phone support in my future.) She’s not signed in, so that’s a dead-giveaway right there.
At any rate, the domain information for “undelivered-emails.com” is cloaked:
Pinging either domain name resolves to IP address is 121.127.225.137, which is in Hong Kong:
As a test, I used a canary virtual machine to see if AVG Free 8.5 would block either of these sites – it didn’t.
BOTTOM LINE
Protection is necessary, but you can’t patch for everything. It comes down to end-user education. If you’re responsible for the computers in your company (or in your home if you’re a parent) you need to let folks know about IM vectors of infection and other threats. Spend the time educating, or spend a lot more time afterwards cleaning up.
TIP
One thing I do to encourage end users to “Call Before Clicking” centers around recognizing them when they make smart web surfing decisions. Example – picking up the phone immediately when getting a “your computer is infected with xyz” pop-ups instead of trying to close the windows.
To assist with this, I have a Microsoft Word document that I can edit called the “Safe Computing Award”. I customize it with the name of the client / employee and send it to them via email when they do something that avoids getting their computer infected. Sample below:
It just takes a minute or two to update the Word doc, PDF it and email it to the customer, and they have always been well received.
A little positive reinforcement goes a long way. 🙂
 Everybody is all excited about the return of Conficker on April 1, 2009, and the news media is whipping the general public up into a froth about it. Even my mom called me to ask about it.
Everybody is all excited about the return of Conficker on April 1, 2009, and the news media is whipping the general public up into a froth about it. Even my mom called me to ask about it.
Here’s the low-down…
PREVENTION:
Microsoft released Security Advisory 967940 to notify users that the updates to allow users to disable AutoPlay/AutoRun capabilities have been deployed via automatic updating channels.
NOTE: Windows 2000, Windows XP, and Windows Server 2003 customers must deploy the update associated with Microsoft Knowledge Base Article 967715 to be able to successfully disable the AutoRun feature. Windows Vista and Windows Server 2008 customers must deploy the security update associated with Microsoft Security Bulletin MS08-038 to be able to successfully disable the AutoRun feature.
CLEANING INFECTED SYSTEMS:
Source: http://technet.microsoft.com/en-us/security/dd452420.aspx
Like a big catfish going after a dough ball, folks are snapping up malware like it’s a $20 bill blowing across a parking lot. Specifically, we’re talking about the old “Antivirus XP”, which is now making the rounds re-branded as “Antivirus Plus”.
Behold…
System Tray
Desktop Icon
Fake Infection Alert
And I’d be willing to bet there are entries in the Quick Launch bar and start menu as well.
ATTENTION PLANET EARTH!
** Antivirus XP 2008, 2009 and Antivirus Plus are SPYWARE! **
They are not helpful programs, and you certainly shouldn’t give these folks your credit card number, OK??
Scroll down for removal instructions. Thank you! 🙂
Props to Kevin Royalty [SBS-MVP] for snapping these pics on his camera phone.
REMOVAL
According to Kevin, our old pal Malwarebytes still gets rid of this nasty. Thanks for the heads-up Kev!